
Pimping My Cousins Wifi From 10 to 100 YouTube
Pwning = Owning. If someone gets your wifi password, they could potentially pwn your network. And if you didn't change your router's admin password, they could completely own (pwn) your entire Internet connection. In theory, they could set up QoS so that their computer would have priority over yours.

What is WiFi? WiFi Working Fullform Routers Standards Explained
Wi-Fi is a wireless networking protocol that devices use to communicate without direct cable connections. It's an industry term that represents a type of wireless local area network (LAN) protocol based on the 802.11 IEEE network standard .

Amrit rana HOW TO SECURE WIFI
Now that you know some of the significant features of Wi-Fi sniffing, this section will discuss a few of its benefits and limitations. Pros Of WiFi Sniffing . It reduces network downtime. Wi-Fi sniffing can help administrators quickly identify and respond to network issues. Therefore, reducing network downtime and minimizing the impact on users.

What is Wifi
Wi-Fi 7 refers to the seventh generation of wireless technology, coming on the heels of Wi-Fi 6 (launched in 2019) and Wi-Fi 6E (2020). It's a collection of technology standards created by the.

'Pimping' Su primer dispositivo WiFi de IoT. Parte 4 IoT
Wi-Fi is a wireless connection to that device, not the internet itself. It also provides access to a local network of connected devices, which is why you can print pictures wirelessly or look at a.

Wifi 6 Here Is Why You Need It Right Now I Tech It Easy Riset
Sep 27, 2021 - Views: 3938 Share Rating: 4.7 - 50 Votes Most internet speed tests display results of 3 parameters: ping speed, download speed, and upload speed. However, ping results are often overlooked compared to download speed. So, What is ping on Wifi? Let's find out its definition as well as its roles.
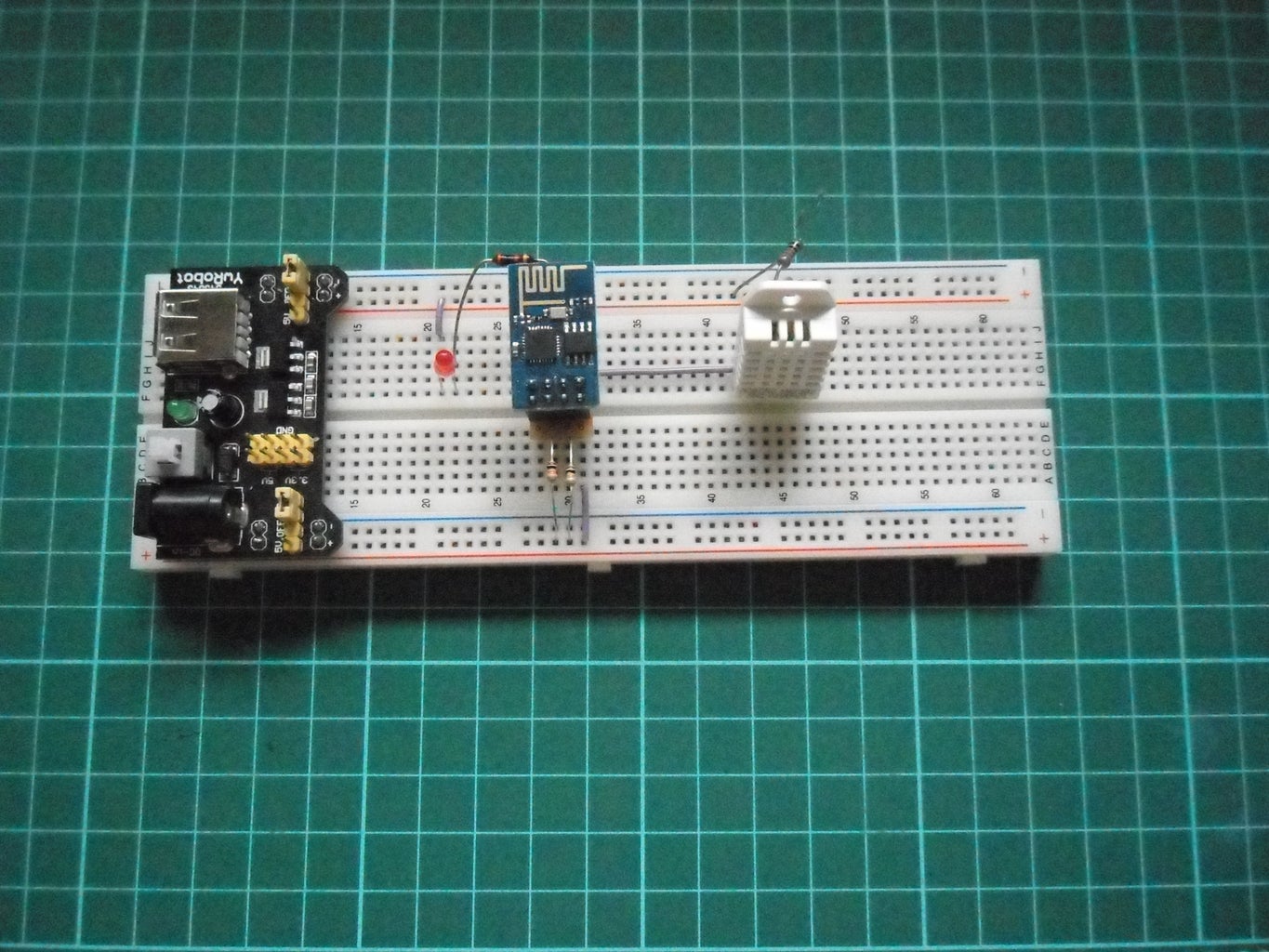
'Pimping' Your First IoT WiFi Device. Part 4 IoT, Home Automation 4
You might unintentionally introduce the malicious software onto your system and invite Wi-Fi eavesdropping and other malign activities. 4. Malicious Hotspots. Malicious hotspots, also known as "rogue access points" or "evil twins", are Wi-Fi networks set up by cybercriminals to deceive users into thinking they are legitimate, safe networks.

Why is my WIFI not working?
Wi-Fi 6 is able to keep a step ahead of the devices in your home to allow simultaneous 4K video streaming, gaming and use by a wide variety of smart home devices, like locks, thermostats and.
Understanding WiFi and How It Works
Scroll down, and look for the Wi-Fi details under Properties. Under that, look for Security Type, which displays your Wi-Fi protocol. Wi-Fi Security on macOS: How to Know Which Type You're Using. Checking the Wi-Fi security type on macOS is very easy. Hold down the Option key and click on the Wi-Fi icon in the toolbar. It will show your network.
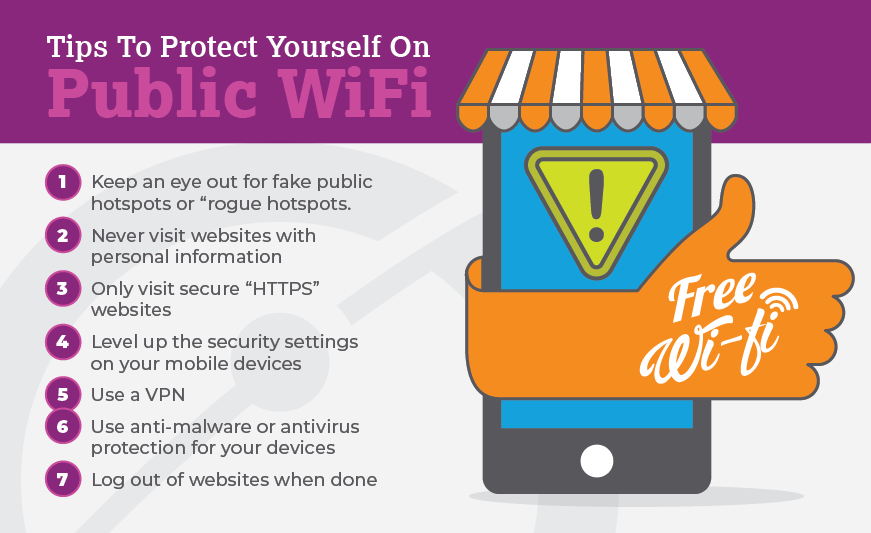
Public WiFi How to Stay Secure and Avoid the Risks of Convenience
Wi-Fi is near-ubiquitous these days, and not just for computers. The modern connected house has smartphones, tablets, Internet TVs and radios, games consoles, AI services such as Alexa and Siri.
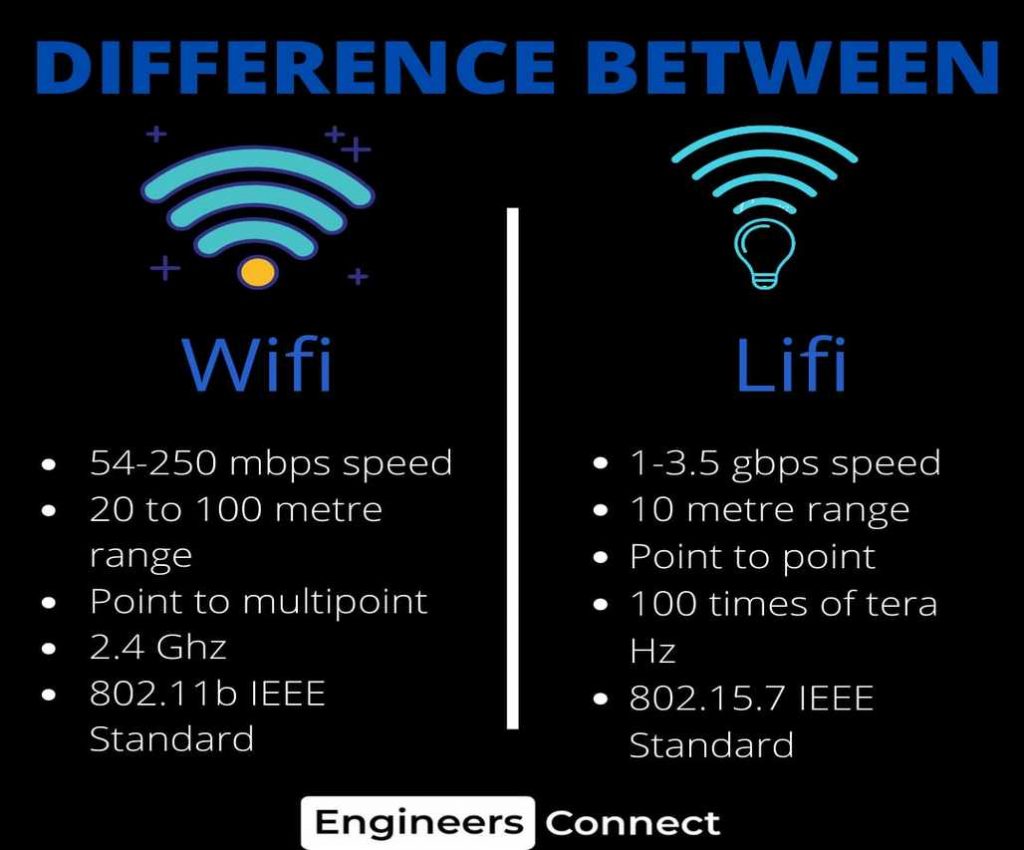
ENGINEERINGCONNECT IS BACK WITH ANOTHER UPDATE WHERE IT GIVES THE
In today's video we are finally fixing my cousin's wifi. It has been pretty bad for a number of years and he kept complaining but never actually did anything.

How to improve your WiFi Signal Stepbystep guide India TV News
Bad wifi in the place I'm staying? Nah man. We gotta fix that up!Crunchyroll link: http://crunchyroll.com/linusIntel link: http://linustechtips.com/main/topi.

What Is Wireless Communication. Why Wireless Technology Is Useful
This Instructable documents how simple it is to extend and further develop an IoT device (pictured above) and is based around the ESP8266-01 WiFi enabled module from the earlier Instructable 'Creating your first IoT WiFi Device. Part 3 : IoT, Home Automation'

WiFi 5 VS. WiFi 6 What Are The Differences
What does Wi-Fi piggybacking actually mean? Find out inside PCMag's comprehensive tech and computer-related encyclopedia.

PIMP your DJI Mini 3 Pro Controller YouTube
WiFi piggybacking is a type of cybercrime in which an individual uses another person's WiFi network without authorization. It involves accessing the internet connection of someone else's home or business, typically by using their password and username to log in. This can be done either intentionally or unintentionally, as some users may not.

Technology of Wifi 6 The Next Generation Wifi Technology
Wifi Phishing is when cyber criminals create a malicious WiFi access point that appears similar or identical to a legitimate WiFi access point. This malicious WiFi access point is sometimes known as the "evil twin". Unsuspecting users can be fooled into connecting to the malicious WiFI point in the belief it is the legitimate connection.